-
impact
Why Forward?Our vendor-agnostic "digital twin" of your network is the most-awarded network modeling software of its kind.
customer storiesSee why the world’s most critical networks depend on Forward Networks
technologyLearn what makes our platform so powerful: header space analysis, mathematical modeling, and all about Network Query Engine
-
additional links
digital twin technologyExplore the mathematically-accurate modeling technology at the core of Forward Enterprise
-
discover forward
forward enterpriseForward Networks’ flagship product, Forward Enterprise, delivers a vendor-agnostic “digital twin” of the network, designed for both cloud and on-prem networks
recognized by gartner
Read the Garner ReportsFeatured in Gartner research publications and industry reports, Forward Enterprise remains at the forefront of technological innovation.
-
platform highlights
network securityDelivering vulnerability management, attack surface management, and stronger security posture through the digital twin model
multi-cloudGain end-to-end visibility, service assurance and continuously audit your entire cloud estate with Forward Enterprise and Forward Cloud
network data intelligenceTrue network reliability, agility, and security by collecting and organizing network data to make it useful and actionable
-
more from forward
Forward Enterprise for FederalLearn how network digital twin technology enables agencies to navigate quickly evolving guidance, cyber threats, and perimeters
play forward quest for freeBegin your quest—Test drive Forward Enterprise in our free browser game
-
solutions
overviewForward Networks can help solve a spectrum of network challenges. Explore by use case, technology or industry.
federal solutionsForward Enterprise provides unified visibility across agency estates, ensures network resiliency, and expedites remediation
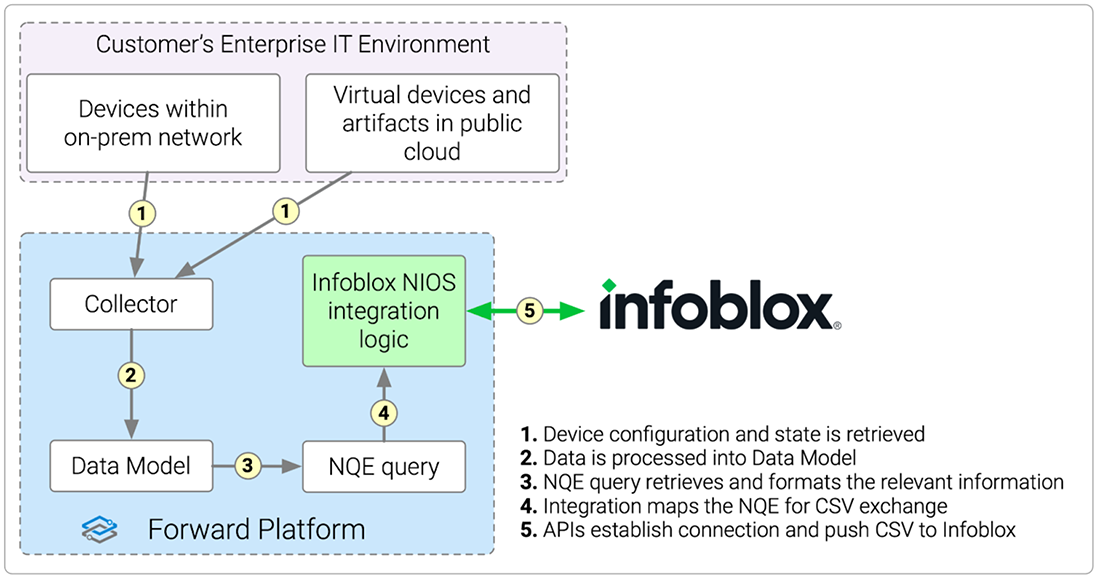
Technology PartnersAPI Integrations that enhance efficiency through seamless data exchange with the Forward Enterprise platform
-
solution examples
universal iTExplore ways Forward Enterprise can improve Inventory management, change control, compliance + auditing, and workflow
network securityDelivering vulnerability management, attack surface management, and stronger security posture through the digital twin model
multi-cloudGain end-to-end visibility, service assurance and continuously audit your entire cloud estate with Forward Enterprise and Forward Cloud
Network OperationsPrevent configuration drift and expedite troubleshooting with unparalleled path verification
-
resources
press roomNews articles, press release, and the latest downloadable content
resource libraryExplore Forward Networks data sheets, whitepapers, ebooks, videos, and more
eventsTalk one on one in-person or virtually with Forward product experts and technical architects
blogRead the latest product updates, query tips, and customer use cases on the Forward Blog
User CommunityCollaborate, learn, and grow: your hub for NQE, network visibility, and security.
Customer Support PortalNeed product support? Login to the Forward Networks Support Portal.
-
Digital Twin Technology
What is a digital twin?Explore the mathematically-accurate modeling technology at the core of Forward Enterprise.
The ROI of a Digital TwinThe financial return on aligning your team, simplifying troubleshooting, ensuring compliance, and avoiding outages.
Recognized by Gartner
Read the Gartner ReportDiscover how to start increasing agility and lowering risk with network digital twin technology.
See for yourself
Network Digital Twin WebinarTop 5 network issuse a Digital Twin can solve in under a week.
Network Digital Twin eBookRead Use Cases on how teams are boosting collaboration and efficiency with Digital Twin technology.